Privacy - Security Nexus in Liquid Staking

This article was co-authored by Nika Koreli, co-founder and CTO of Hinkal, and Shota Natenadze research & governance analyst at Simply Staking.
Time to Reconsider Privacy and Security in DeFi?
Liquid staking has revolutionized DeFi, enabling holders to pursue further profits. However, tokenized positions, especially for significant holders, entail several risks, not confined to Lido’s protocol exposure. Transactions and assets held are publicly visible, which makes users prime targets for hacking attempts, as their assets and activities are exposed. This exposure also reveals their strategies, leading to reduced yields due to widespread copying. Additionally, users become vulnerable to copy-trading, where others replicate their trades, and MEV attacks, where malicious actors exploit transaction ordering for profit. Furthermore, their activities can inadvertently provide market signals, tipping off competitors and compromising their competitive edge.
In DeFi, discreet transactions and network security are inherently complementary, each addressing critical aspects of user trust and system integrity. Not publicly disclosing transaction information ensures that sensitive financial activities remain confidential, protecting users from potential exploitation and safeguarding personal information. However, this is only as valuable as the robustness of the underlying protocol. If a liquid staking protocol fails, via Syibil or Grinding attack, for example, disclosing a user's transaction information likely becomes less important in the face of potential liquidations or systemic collapses. On the other hand, even the most secure protocol could lose user trust if transactions are fully transparent and vulnerable to malicious actors. Therefore, achieving a balance between discreetness and security is essential. Robust protocol design ensures the stability and reliability of DeFi systems, while strong measures to protect individuals’ transaction data keep users safe from public exposure and targeted attacks.
Introducing Hinkal: Secure. Discreet. Decentralized.
On-chain data analytics tools like Arkham, Nansen, and DeBank have widely affected the DeFi landscape. The pseudonymity once afforded to on-chain transactions is now a thing of the past. These tools not only track the assets and transaction histories of entities and individuals but also link them with off-chain information. While they aim to provide transparency, they have inadvertently made doxxing—the exposure of someone's personal information online—easier than ever. This creates easy targets for malicious actors to exploit.
With on-chain activity now easily traceable, significant token holders face risks such as copy-trading, front-running, and being targeted by hackers. Additionally, yield strategies can be widely mimicked, diminishing their effectiveness and cutting into investors' profits.
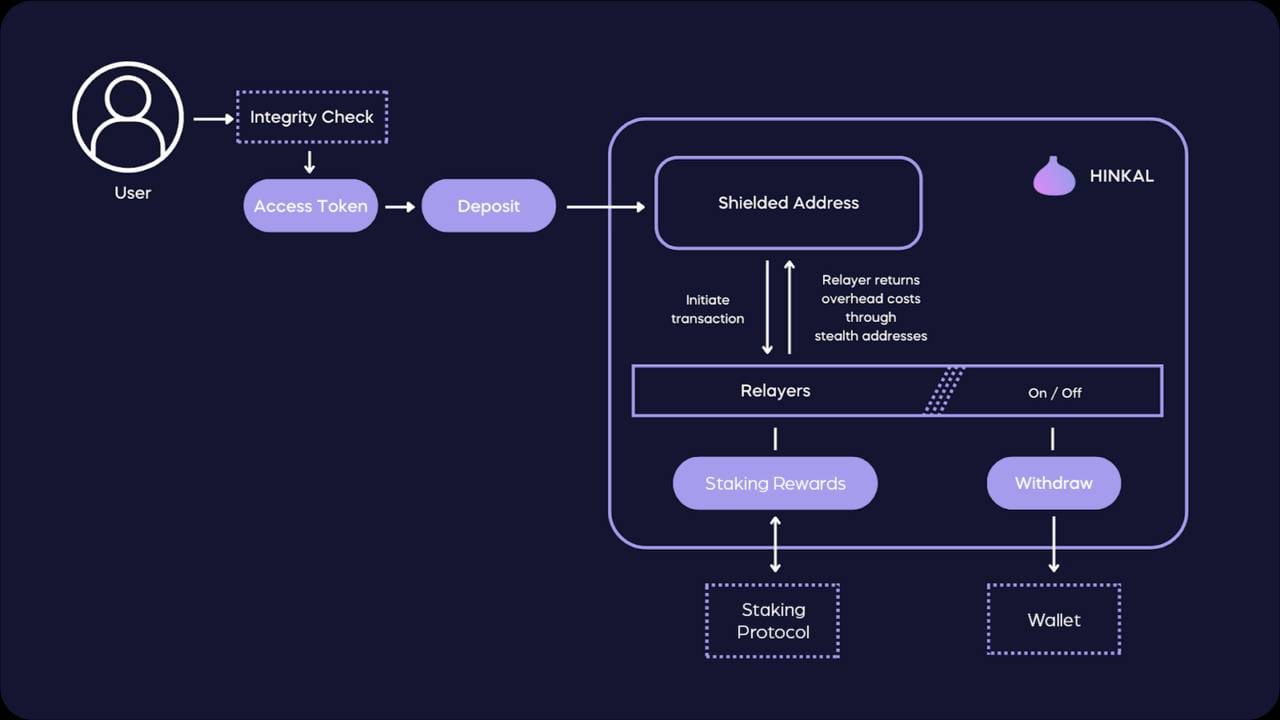
Hinkal, an institutional-grade ZK protocol, addresses this dilemma, employing shielded addresses, stealth addresses, relayers, and Integrity Checks to enable discreet transactions, without disclosing transaction information to the public. This self-custodial approach allows users to conduct transactions without any connection to their wallet or record of previous transactions.
Instead of initiating transactions directly from their wallets, users route their transactions through a relayer, leveraging ZK technology to verify fund ownership without disclosing the owners' identities. The relayer executes the transaction on their behalf and returns the exchanged assets to shielded addresses within the smart contract. This ensures that assets remain under the user's complete custody while enabling discreet interactions with major dApps through a unified interface.
Hinkal’s smart contracts have undergone multiple audits by Quanstamp, Secure3, and Zokyo, complemented by inspections from whitehats. Immunefi’s bug bounty program ensures that no vulnerabilities go unnoticed. Hexagate's real-time threat detection, coupled with an AML/KYC layer, further strengthens security measures, while a password-protected mode provides an additional layer of account protection.
If Proof of Stake, Then Why Trust?
While Hinkal addresses the privacy concerns in liquid staking, it is equally crucial to consider the security aspects within the PoS paradigm. A growing appetite for higher returns and flexible liquidity has spurred the development of staking solutions designed to maximize returns and attract users, thereby increasing their Total Value Locked (TVL). However, there is no free lunch, as many of these solutions, such as restaking and liquid staking, trade security for greater profitability. Even if engaging with a protocol is both profitable and discrete, security vulnerabilities could affect the value of the staking token, lead to a network fork, or significantly delay the unbonding period of the staked assets, therefore translating into a financial risk. Consequently, the scalable performance of high-quality and robust validators is essential to ensure the sustainable performance of the network, hence producing a secure, high-yield, and discrete environment for retail and institutional users. Below, we review the mentioned security risks in more detail and discuss how Simply mitigates these.
In proof of stake protocols, users delegate their staking power to validators through smart contracts and expect them to act in the network's best interest to earn rewards and avoid penalties. To avoid the principle-agent fallacy, validators in PoS systems are subject to slashing conditions where their staked assets can be partially or fully forfeited for malicious behavior, hence becoming a disincentive for misconduct. In protocols that inherit security from an L1, the security of the entire staking mechanism relies on core validators being trustworthy, as any slashing incident directly impacts the value of staked assets. Simply Staking has fostered community trust and interest alignment by actively participating in both on and off-chain governance, this is why Simply’s uptime participation rate stands at 99.9%, with 98.2% governance correctness.
Further, the value of liquid ETH tokens such as should ideally reflect the value of staked ETH, considering accrued rewards minus potential penalties and operational intricacies such as divergence in Oracle price data and friction. If the underlying validators perform poorly or get slashed, the value of liquid ETH will also deteriorate. Therefore, for liquid staking to continue to thrive, it must consistently instill confidence in both the underlying staked asset (ETH) and the derivative token. To this end, strong economic security through diligent and secure staking practices by validators ensures that market participants trust the value and stability of the derived ETH, fostering greater adoption and liquidity. Simply Staking has set up redundant systems and failover mechanisms to ensure high availability and minimize downtime, while consistently undertaking manual software updates and running automatic 24/7 security alerts to maintain the integrity of validator technology.
To mitigate risks associated with slashing and validator failures, liquid staking solutions could employ multiple insurance mechanisms, such as partial allocation of staking rewards to an insurance fund that can compensate users in case of significant losses. Further, in the event of a validator underperforming or facing slashing penalties, most protocols have mechanisms to replace such validators promptly, ensuring that the overall staking process remains secure and efficient, minimizing downtime and potential losses. To hedge against slashing and removal risks, Simply Staking has not only passed all Operator Requirements on major staking solutions like Lido but also employs a robust disaster recovery process, where keys can be moved from one node to another. Simply’s backup nodes are running across three data centers in Malta, the Netherlands, and Canada, with 24/7 security alerts that go straight to the DevOps team.
Although multiple validator-side risks exist in liquid stalking protocols, including downtime, slashing, and the principle-agent problem, that in turn affect both the value of the staked assets and staking yield, Simply Staking has been able to mitigate these through active governance and cutting-edge internal security measures. Therefore, maintaining nearly 100% uptime on Lido and securing more than USD 1 billion in assets under management across 60+ networks and ecosystems.
When Security Meets Privacy
Institutional and private investors often develop unique on-chain financial strategies to maximize returns, incorporating staking with other DeFi actions like trading. However, maintaining the competitiveness of these strategies requires discretion to prevent them from being cloned, as the blockchain is inherently an open-source database. Thus, investors can benefit from using Hinkal to make their on-chain strategies, including staking portfolios, less visible. To ensure these strategies are performable and secure, it is essential to operate on chains and protocols that are safe. Delegating to robust validators like Simply Staking through Hinkal provides investors with the best of both worlds: minimizing security and infrastructural risks while keeping their strategies discreet, thus preserving their competitive advantage.
Let’s explore how Simply Staking’s and Hinkal’s solutions can be combined to provide the optimal experience for users, safeguarding their transaction information, the security of their assets, and ultimately their profits. Users of Simply Staking can enjoy the benefits of discreet delegation of funds and receive their profits by leveraging Hinkal's zk-protocol. When users decide to stake their funds through Simply Staking, the delegation could occur through Hinkal.
Hinkal enables the deposit of assets to any user’s shielded addresses. This allows Simply Staking to receive funds designated for staking directly into their shielded account acting as a discreet vault. From this point, funds can be allocated as intended. This ensures that any linkage between the users’ public wallet and Simply Staking's wallet is severed, maintaining their staking activities and assets undisclosed. All that is visible on-chain is an interaction with Hinkal. Alternatively, users can directly use Hinkal to send funds to Simply Staking's wallet, effectively anonymizing the transaction and ensuring that their public wallet remains unassociated with their staking activities.
When it comes to receiving profits and the principal capital from their staking endeavors, Simply Staking can further protect users’ information by depositing these assets directly into the users' shielded addresses within Hinkal. This scheme effectively allows Simply Staking to provide its high-quality infrastructure, while Hinkal acts as a protective layer for users’ transactions and asset information.
Conclusion
In summary, a combination of privacy-enhancing solutions with staking delegation could address important issues of privacy and security in liquid staking. Hinkal's ZK protocol allows for discreet transactions, protecting user financial activities from public exposure. Simply Staking's governance and security measures ensure the reliability of staking operations. This partnership aims to safeguard user assets and transaction information while maintaining the stability of staking processes. As DeFi evolves, finding the right balance between privacy and security will be crucial for the continued growth and reliability of these systems.




